How to control sensitive data on unmanaged devices with MCAS (Part 2 of 2)
Perficient
MARCH 22, 2021
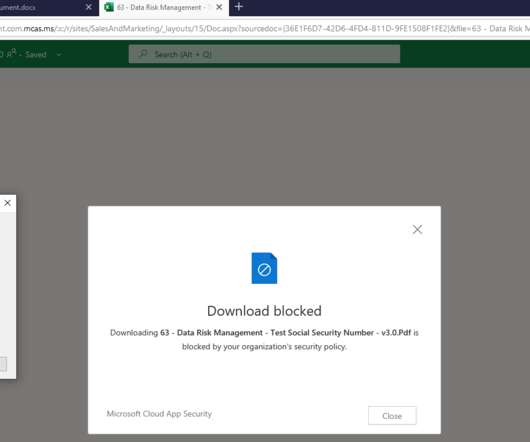
This time we’ll take things a step further and show you how to restrict specific activities like cut/copy, paste, and printing! End-user experience. Attempting to Print: User Experience. Attempting to Cut or Copy: User Experience. Attempting to Paste SSN from Notepad into file: User Experience.












































Let's personalize your content