Securing Teams with built-in apps in Microsoft Endpoint Manager
Perficient
NOVEMBER 15, 2020
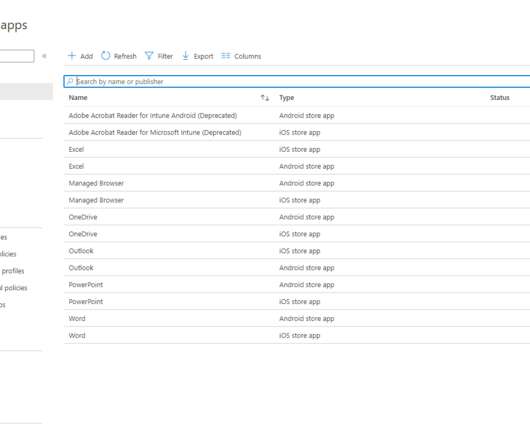
In this blog, we’ll go over four main areas of Endpoint Management: Creating an app deployment. Securing the app (conditional access with MFA). Since my blogs typically cover all things Microsoft Teams, we’ll discuss how you can use Microsoft Endpoint Manager to secure Microsoft Teams! Securing the App.









































Let's personalize your content