How to control sensitive data on unmanaged devices with MCAS (Part 2 of 2)
Perficient
MARCH 22, 2021
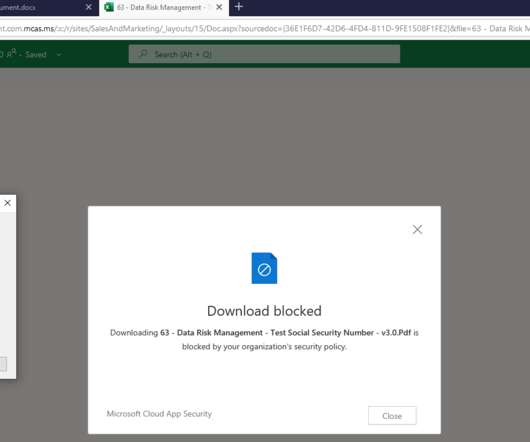
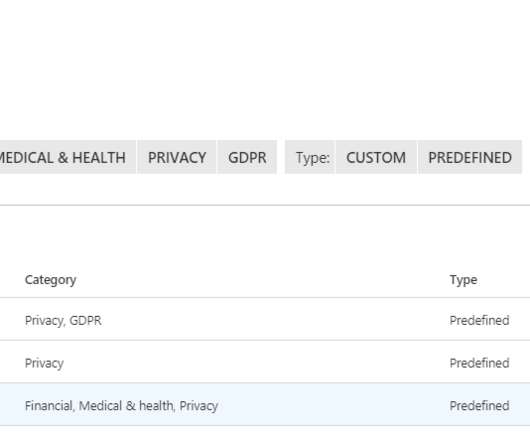
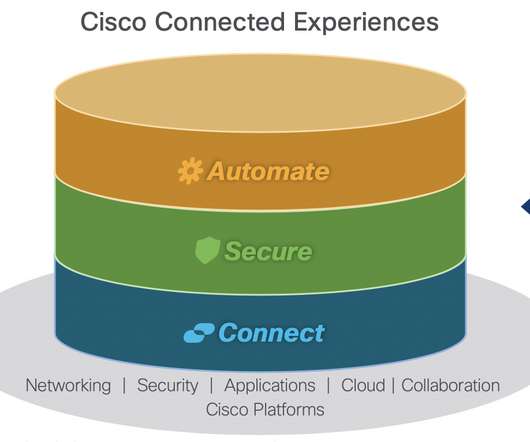
If you are joining us for the first time, I encourage you to check out the first blog for a quick rundown of our scenario. In the first blog, we outlined a scenario where our user Megan B. PII: Social Security Numbers) or custom expressions. End-user experience. Attempting to Print: User Experience.








































Let's personalize your content