How to control sensitive data on unmanaged devices with MCAS (Part 2 of 2)
Perficient
MARCH 22, 2021
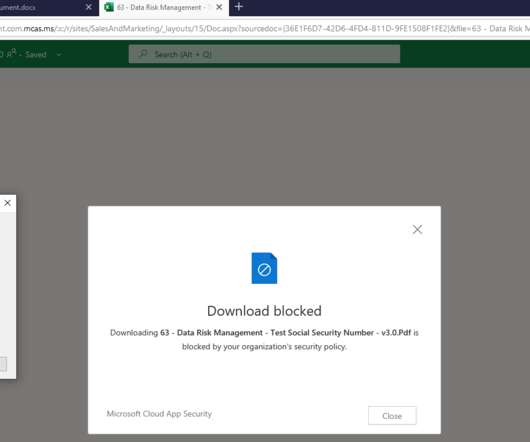
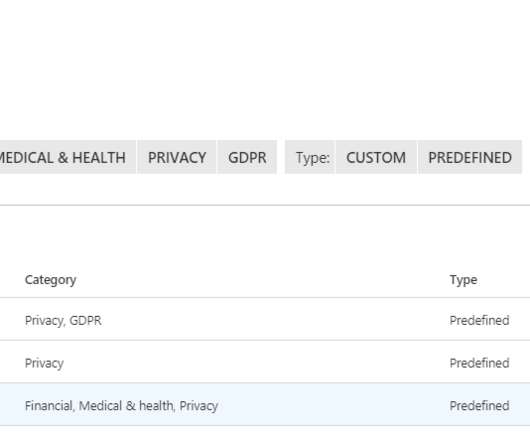
This time we’ll take things a step further and show you how to restrict specific activities like cut/copy, paste, and printing! PII: Social Security Numbers) or custom expressions. For our use case, we’re going to select one of the preset expressions and choose US: PII: Social Security Number. . End-user experience.











































Let's personalize your content