
Shubham Shah learned to hack as a teen. At that time he just wanted to beat his brother at video games, but he's in the big leagues now. In 2022, at the age of 26, he earned his 1 millionth dollar on a popular hacking-for-hire platform.
Shah, known to many hackers as Shubs, has graduated from cheating in video games to breaking into some of the highest-security systems that banks, credit unions and other organizations have built, but he doesn't steal customers' personal information or hold systems for ransom like they do in the movies.
Shubs breaks into PayPal, Goldman Sachs and others by invitation, with a promise from the companies that they will not take him to court for his work, as long as he follows their rules. In exchange, every time he finds a vulnerability in their websites or another system they own, they pay him.
"When I was probably 14, I submitted my first bug to PayPal, and the payout they had for that was around $1,500," Shah said. "That was more than what I had made working eight months in the fast-food industry at the time, so I never showed up to that fast-food job again."
Shah is modest about what he achieved as a middle schooler, saying he was a tyro in his field at the time. A company with a bug bounty does not pay out unless its security team validates the existence of the vulnerability and that it exposes important information.
"I was submitting all sorts of things that technically could be considered security issues, but the security impact was little to none, so they weren't accepted as valid issues," Shah said. "I was really a novice in my field, and I think I got quite lucky when I did find that valid security issue when I was 14."
The discovery changed his life.

"It triggered a series of events that made me very passionate about application security," he said.
Today, Shah is the corporate technology officer of Assetnote, a company he co-founded that helps clients monitor the security of their computer assets, in part by automating some of the hacking he and others have learned to do over the past 12 years.
Last spring, Shah crossed the seven-figure mark on HackerOne, the hacking-for-hire website that manages bug-bounty programs on behalf of companies. He ranks 28th all-time on HackerOne's reputation rankings, which is based on the amount of recognition he has gotten from other hackers on the platform.
"I'm already nearing $1.5 million," he said in December.
Shah embodies one of the primary lines of defense companies have against cybercriminals, who typically share many of the same abilities he has honed as a hacker, with one key difference. Shah works with companies to help them identify weaknesses; cybercriminals exploit those same weaknesses to steal valuable information.
For customers harmed by such cyberhacks, this leads to distress and distrust toward the company to which they had entrusted their data and money.
Any financial institution or other business that employs the services of an ethical hacker puts considerable trust in that individual. The company allows someone outside the organization to try to infiltrate its defenses to make the system better, often in exchange for payment.
Sometimes ethical hackers even show up uninvited when they stumble across a vulnerability, leaving financial institutions to decide whether to thank them or try to prosecute. Regardless of how a bank or credit union comes to work with an ethical hacker, understanding goes a long way toward establishing trust.
A penchant for bending the rules
Krissy Safi had strict parents growing up, and she had to be clever to get around them. She said she was a good kid, but they just had a lot of rules. For example, she wasn't allowed to read books when they grounded her.
Safi figured out that having the lights on in her room would tip her parents off to whether she was reading, so she created a small reading lamp by attaching Christmas lights to a book cover and powering them using a 9-volt battery. It created just enough light to illuminate the pages but not so much to tip off her parents to her covert activities.
"My brain has just always kind of worked that way," Safi said. "How can I get this thing to work in a way that I want it to? How can I circumvent somebody's rules, or use something in a way it wasn't intended?"
Safi's parents gifted her an Apple Macintosh when she was in sixth grade, when she started to acquire a taste for hacking

"America Online was sending out their discs to get free internet, so working with some groups in message boards, I learned how to circumvent some of America Online's rules so I could be online more often," Safi said.
Her parents caught on to her late-night internet browsing and took away her dial-up modem. So, Safi got her own with money she got working as a babysitter for families around town.
"I would hide it during the day, and when they would take the other modem at night, I would plug in my own and wrap it in a pillow," she said. "Of course, it would get really hot, but I had to do that because it made that loud noise."
Eventually, she started school at the University of Colorado at Boulder, pursuing a degree in mathematics. Along the way, she got a job repairing computers for the university — something that started after many episodes of her fixing lab computers so she and her classmates could complete assignments. Eventually, IBM found her and offered an internship.
"I'd walk around this building with 9,000 employees in north Boulder with my little clipboard and be like, 'OK, please show me that you have a power-on password. Please show me your Lotus Notes Databases are encrypted,' " Safi said. "I met a lot of people, including the team that was doing pentesting, and I was like, 'Oh, wow, you can do this as a job!' "
Penetration testing, also known as pentesting, involves evaluating the security of computer systems by attempting to hack them. After expressing an interest in doing more of it, the pentesting manager switched Safi into his department, and she decided she wanted to keep doing the work after graduation. She asked her manager what she needed to do to move up from the internship into a full-time job.
"Back in the early 2000s, there weren't really degrees in cybersecurity," Safi said, "So he just told me to take my fastest way out of school. I went back to my counselor, and she said it was Italian."
Safi graduated with a degree in Italian and started working for a manager with a degree in financial affairs and a team lead with a degree in Russian. She eventually helped IBM build out its X-Force Red Offensive Security practice, which provides pentesting services, and is now global lead for the consulting firm Protiviti's attack and penetration testing services.
Safi today does less hacking and more management, but she has stuck to pentesting because of the challenges associated with it, the thrill of doing what would ordinarily be illegal in the absence of permission from companies to perform the hacking, and because it ensures that people have their information securely kept.
"As an individual, for example, it's nice to know that companies are invested in solving their security issues and doing the right thing to prevent identity theft," Safi said. "For me, it's about being altruistic and doing the right thing."
Driven to help rather than harm
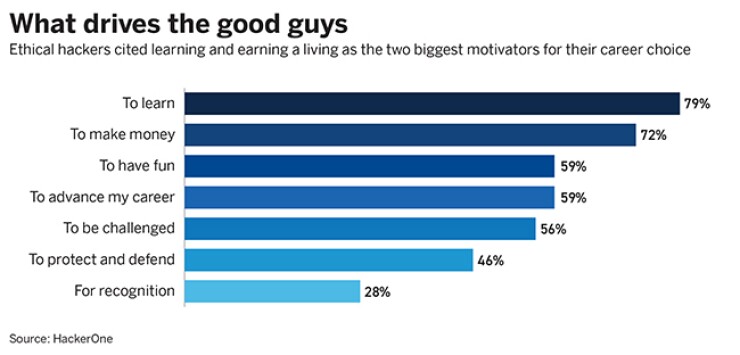
In an annual survey this September, HackerOne asked more than 5,700 hackers why they do what they do and allowed them to select multiple responses. The motivation to learn came in first (79%) and making money came in second (72%). Other popular motivations hackers cited were advancing their career (59%), having fun (59%) and being challenged (56%). Shah and Safi share many of these same motivations.
Shah has seen bug-bounty programs grow in popularity since he got his first payday participating in one. PayPal was among the first to implement such a program, in 2012; government agencies, financial institutions and others have since launched their own.
However, most bank-run bug bounties are private, according to Julien Bonnay, the U.S. head of technology and cybersecurity for the financial services consultant Capco. Bonnay estimates roughly 80% of banks' bug bounties are invite-only, allowing them to have well-known and identity-verified hackers participate, to give the institutions more control over who is scrutinizing their security systems.
Financial institutions often find the hackers to invite to these private programs by seeking out the top performers on hacker platforms like Bugcrowd and HackerOne. Hackers can also earn an invite to a private program by finding and responsibly disclosing a vulnerability to an institution via public means.
These public channels are also known as vulnerability disclosure programs. They are like a bug-bounty program, but without the promise of payment. VDPs draw less attention from ethical hackers who can instead pursue paid opportunities, but a VDP provides a way to responsibly report any bugs they do find — whether by accident or in hopes of landing an invite to a bug-bounty program.
Having a public VDP while maintaining a private bug-bounty program gives institutions a greater level of control over who gets involved and limits how much work the bank's security team has to take on and fix, according to Bonnay.
"Banks make these programs private to manage the number of reports they get sent back," Bonnay said. "The more public it is, the more likely it is you'll get redundant vulnerabilities being reported, which can be painful for the banks to manage. There's also the risk that there are some bad actors or actors who are not as knowledgeable as the ones who have been vetted, and they go too far or don't respect the rules."
However, this commitment to secrecy also has detractors. Katie Moussouris, CEO and founder of the cybersecurity consultancy Luta Security, is one of them.
Responsibly wielding power
Moussouris got her start "robbing banks" by hacking them, she said. She also hacked credit card companies and once found a bug she claimed would have allowed her to authorize any transaction she wanted. Rather than exploit it, she reported it to the company (which she did not name), and the company fixed it.
In 2021, Moussouris found a security vulnerability at the social media platform Clubhouse that allowed users to secretly remain in a voice chatroom even after being removed, without the moderator having the ability to kick them out or mute them.
For weeks, she said, the company did not take her emails about the vulnerability seriously, but a Clubhouse spokeswoman said the company initially responded within five days. Moussouris felt the flaw was serious enough that she set a date of when she would publicly tell people about the vulnerability so users would be warned. That's when she said she finally got action.

"They finally answered me because I said, 'Look, I'm going to disclose this vulnerability to the world because you guys aren't taking security seriously at all and I haven't even gotten a person to respond to me,' " Moussouris said.
Clubhouse encouraged Moussouris to go through the company's private bug-bounty program, which it had set up to deal with this kind of discovery. Moussouris declined. Although she could get paid by participating, she did not want to sign the required nondisclosure agreement.
Instead, she told Clubhouse that if the vulnerability qualified for a bug bounty, the company should donate the fee she would otherwise receive to Pay Equity Now, a nonprofit she started to help close the gender and racial pay gaps, or to a charity of Clubhouse's choosing.
"I will not accept your bug-bounty nondisclosure terms, because I would find that to be against my own code of ethics to protecting users," she told Clubhouse.
After Moussouris submitted the findings to the company in early March, Clubhouse fixed the vulnerability in April.
Clubhouse has since changed its disclosure terms to match those HackerOne uses in VDPs and turned its private bug-bounty program public. Clubhouse also said it appreciated "the collaboration of researchers like Katie, who helped us identify a few bugs in the user experience and allowed us to swiftly address those to remove any vulnerability before any users were affected."
Hackers teaching hackers
Other hackers share Moussouris's disdain for nondisclosure programs. In HackerOne's survey, 11% of hackers said they would decline to participate in a bug-bounty program if it came with an NDA, though much more common turn-offs include slow response times from the hacked company (51%) and low payouts in exchange for the work (46%).
Nondisclosure agreements, which are common in financial institutions' programs, do more than just violate the code of ethics for some hackers. For seasoned professionals hoping to share their knowledge with novices, a contract that prevents them from providing details of how they discovered a vulnerability becomes one less lesson from which other hackers can learn.
"I'm very grateful for the amount of things that I've learned, and that's only been possible because of people that have explained vulnerabilities publicly, explaining how they discovered it and things like that," Shah said. "That often leads to people like myself, who are learning about these things, to be able to discover them and other attack surfaces."
For Shah, writing about vulnerabilities is more than just a teaching moment. It's a way to build clout, which is vital for someone trying to break into the world of invite-only bug-bounty programs.
"When I started doing bug bounties, writing about vulnerabilities was incredibly important to me because it helped me build a reputation and break into the industry," Shah said. "That's how I got my first job."
While most distributed denial-of-service attacks against U.S. banks and credit unions result in little to no disruption, they can chip away at reputations if left unchecked.
Shah enjoys blogging about vulnerabilities on his personal website and on company blogs, a practice common among security researchers and companies engaged in such work. However, nondisclosure agreements hinder thought leaders like Shah. That's why, he said, many hackers opt instead to go for coordinated disclosures, as Moussouris did with Clubhouse.
"In that scenario, you're basically able to attach terms that say you can publicly disclose after 90 days," Shah said. "This is not to say that bug-bounty programs do not allow disclosure, wholesale. There are a lot of bug-bounty programs that are quite open to that sort of thing. But I've never experienced that with banks specifically."
A hacker can say that an institution has 90 days to fix a vulnerability before publicly divulging the secret, and for the vulnerable bank or credit union, that might come off as extortion or a threat. However, it is well within the boundaries of normal security research to do that, according to Kayne McGladrey, a senior member of the Institute of Electrical and Electronics Engineers and a field information security chief for the security and compliance company Hyperproof.
"If the company doesn't respond in a timely manner, that's where you can get vulnerability disclosures after a reasonable period of time, like 90 or 120 days, or 180 days, depending on which philosophy the researcher subscribes to," McGladrey said. "That's all well within the ethical boundaries of a normal security researcher."
The key difference between an ethical and unethical hacker — between extortion and responsible disclosure — is what the hacker does with the vulnerability.
"I think it's very possible to say you can prove you can use this vulnerability — maybe it's to steal a whole bunch of credit card information — without actually doing it," McGladrey said. "You just show that you can."






