Welcome back! Last time we talked about controlling file downloads of sensitive content by using a session policy in MCAS. This time we’ll take things a step further and show you how to restrict specific activities like cut/copy, paste, and printing! If you are joining us for the first time, I encourage you to check out the first blog for a quick rundown of our scenario. Without further ado let’s jump back into things!
Scenario Recap
In the first blog, we outlined a scenario where our user Megan B. was attempting to download an Excel file that contained sensitive information from her personal laptop. Without proper protection in place, Megan B. would have the ability to easily download any content to her personal device which could result in sensitive information leaving your organization for good. However, once we implemented the proper session policy in MCAS, we were able to look for files that contained sensitive information (in our case SSNs) and block anyone on an unmanaged device from downloading the file.
Blocking Cut/Copy and Printing in MCAS
In this blog, we’re going to change things up a bit and instead of only blocking downloads we’re going to create another session policy to block cut/copy, paste, and print activities of sensitive data on an unmanaged device. To create the session policy, we’ll do the following:
- Navigate to portal.cloudappsecurity.com
- On the left-hand side, find the Control drop-down and select Policies
- Find Create Policy drop-down and select Session Policy
- On the “Create session policy” page, select the Policy template drop-down and choose the Block cut/copy and paste based on real-time content inspection
- Select Apply template
- Find Session Control Type and in the drop-down to select the type of control you want to enable, select Block Activities.
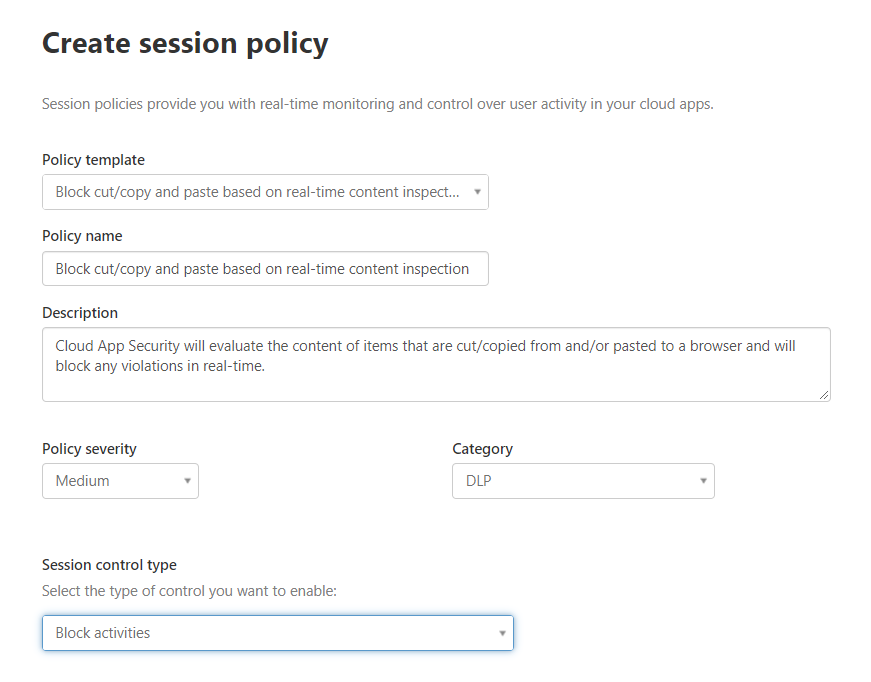
- Under Activity Source we’ll choose the corresponding filters that we want to match on. First, we’ll choose our activity type which will equal Print, Cut/Copy item, and Paste item. In addition, we’ll want to find all devices that aren’t Intune compliant nor hybrid Azure AD joined. Lastly, we’re only going to look at Teams, Exchange, and SharePoint Online for our apps. Once all of those filters have been configured, it should look similar to this:
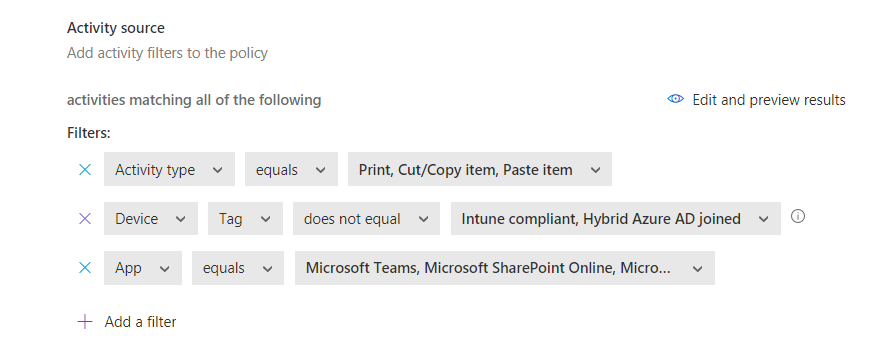
- We can take things a step further by using content inspection. This can include text matches for preset expressions (i.e. PII: Social Security Numbers) or custom expressions. You also have the ability to exclude text that matches a regular expression. For our use case, we’re going to select one of the preset expressions and choose US: PII: Social Security Number.
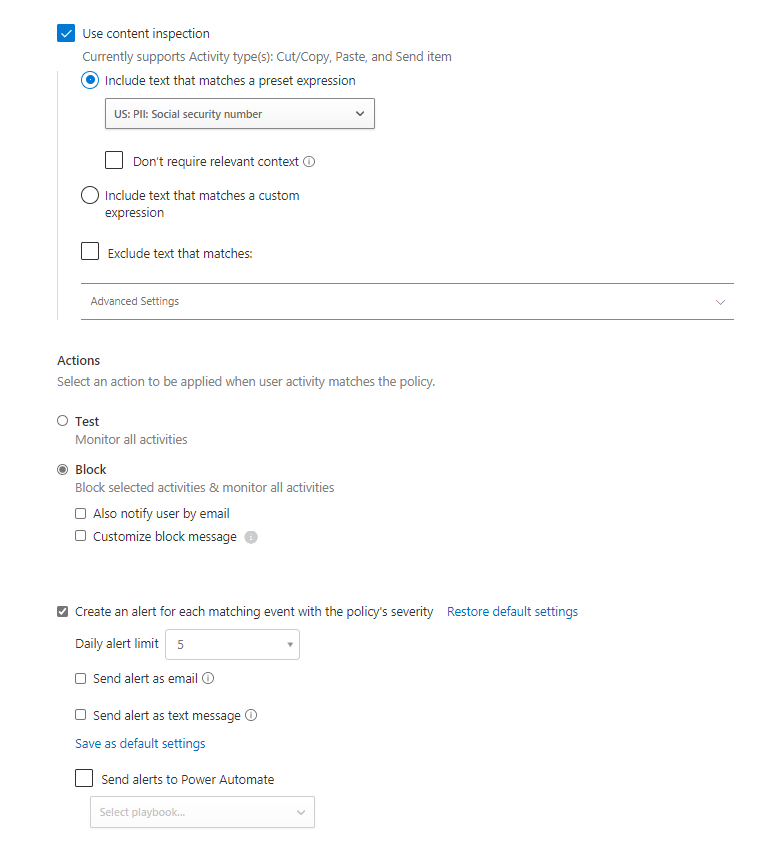
- Next, we’ll configure our actions, and as mentioned we’re going to select Block. You can also have the user notified via email when the block occurs and customize the block message to your liking.
- Last but not least, you’ll set your alert limit. The default will be 5 daily alerts, but this can be increased to as many as 1000 daily alerts! You can also send the alerts as an email to the email address of your choosing and/or send the alert via text message! If you’re even feeling wild enough, you can use Power Automate to send your alerts!
End-user experience
Now comes the fun part…testing! Just like with our last scenario, when Megan navigates to SharePoint Online she immediately sees a screen letting her know that her access to SharePoint Online is being monitored and that access will only be available from a web browser. Once she selects Continue to Microsoft SharePoint Online, she will be proxied through MCAS but from the end-users perspective, everything will look the exact same.

A good way to tell that this has successfully been forced through MCAS is by looking in the address bar once the page has loaded. You should see mcas.ms in the address.

Megan B. has now reached the SharePoint site from her personal laptop and proceeds to open the Excel file that contains several different SSNs.


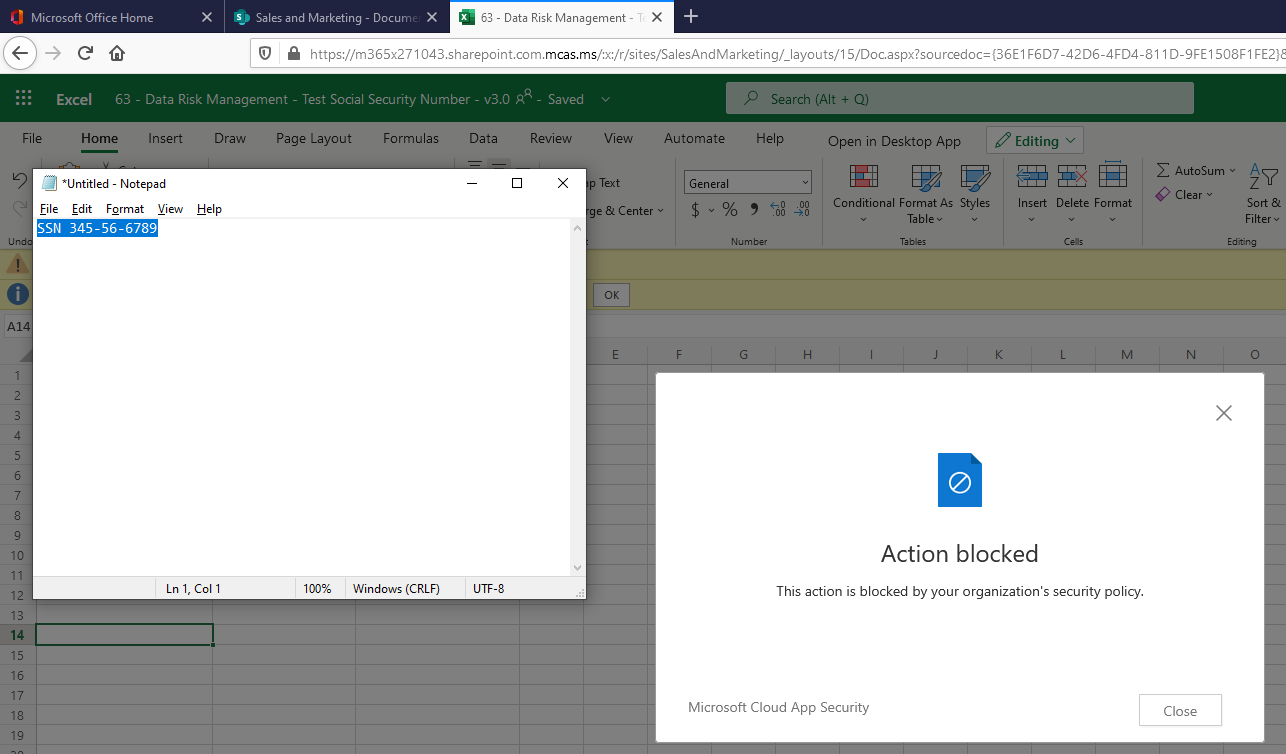
Previously, Megan B. would be able to cut/copy, paste, or even print this file, in which case you could kiss that sensitive information goodbye as it just left your organization for good. However, with the new Session Policy in place, when Megan B. attempts to cut/copy, paste, or print this file on her personal/unmanaged device she will be blocked from doing this and will receive a pop-up informing her that the action was blocked by the organization’s security policy.
Attempting to Print: User Experience
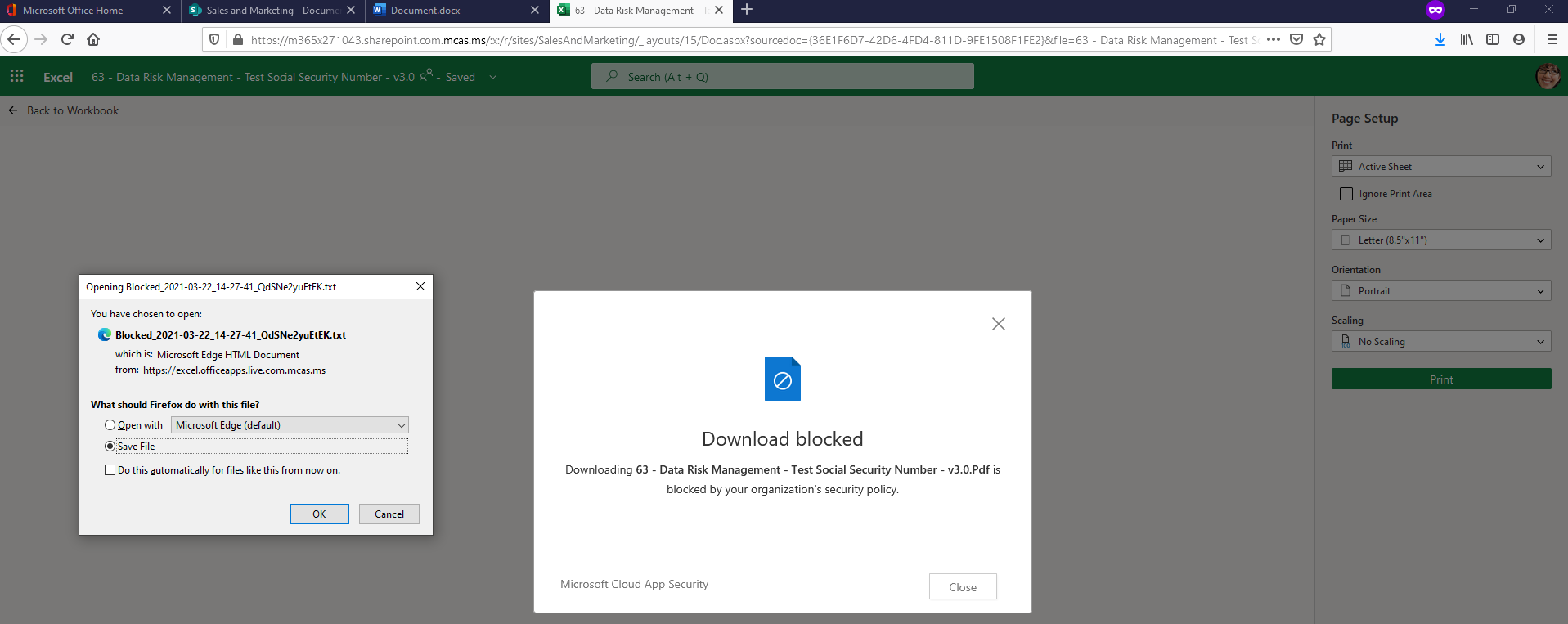
Attempting to Cut or Copy: User Experience
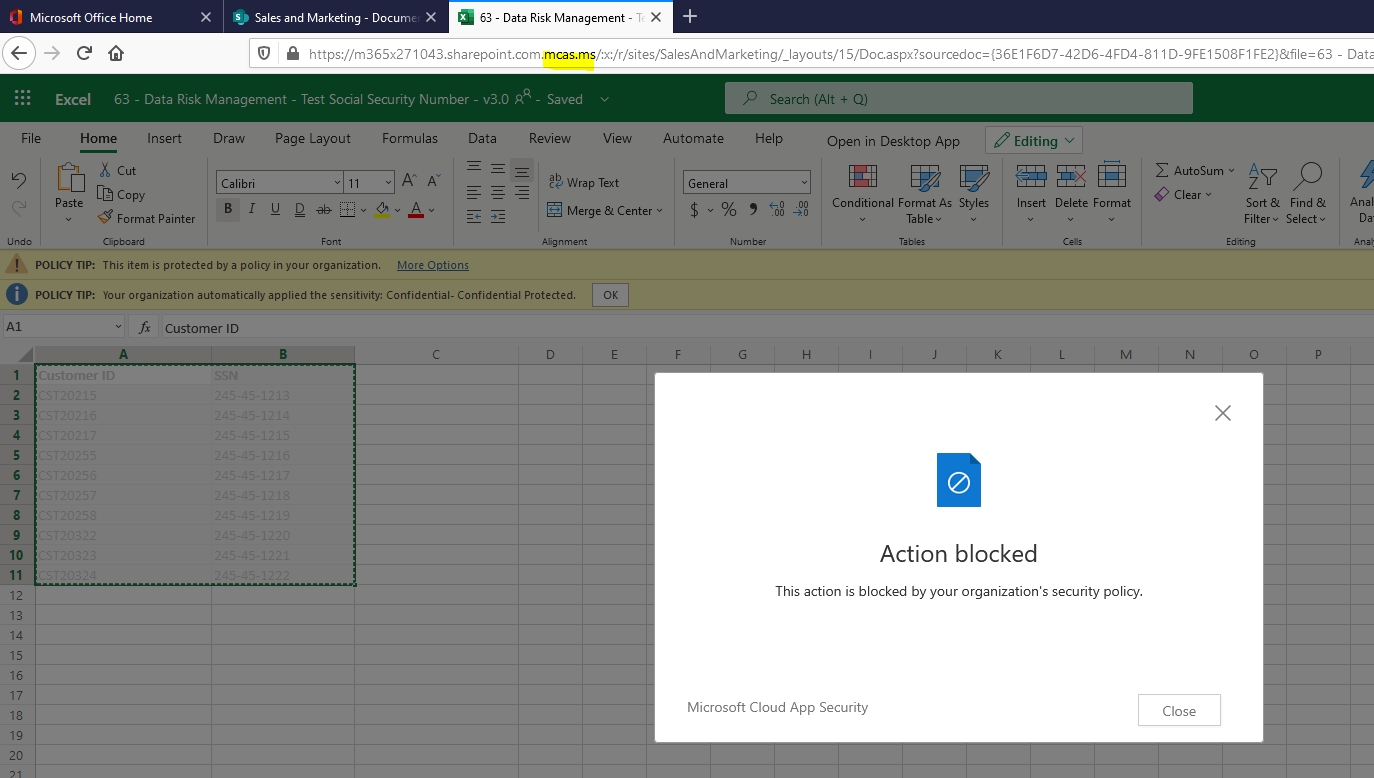
Attempting to Paste SSN from Notepad into file: User Experience
As you can see, there are various ways that someone could try to exfiltrate sensitive information, but with MCAS we can stop many of these actions from ever occurring. I hope you have found this second blog as helpful as the first, and I hope you’ll check back shortly for more MCAS scenarios like this one!





Hello there:
Do you know if there’s a way to allwow copy/paste between MS services, but block it externally?