Two-factor authentication (2FA) is a commonly used tool to add an extra layer of security and prevent unauthorized login of online accounts. Many websites now leverage one-time passwords (OTP) to authenticate a login and verify the user’s identity. Not surprisingly, cybercriminals and fraudsters have consistently developed various techniques to bypass and defeat 2FA. OTP bot services have become increasingly popular with cybercriminals and fraudsters in recent months. OTP bots communicate automatedly with victims, attempting to trick them into providing information required for account takeover. These services use bots to initiate phone calls to the victims and solicit sensitive information such as 2FA codes, account PINs, and other PII. For the most part, these bot services are provided as a service, and they are available in various underground communities and telegram channels. Any threat actor willing to pay can get immediate access to these bots.
OTP Bots Are a Growing Threat: What Financial Institutions Need to Know
OTP bots are the latest fincrime trend.
Financial institutions must know how to combat the threat of OTP bots and educate their customers.
Takeaway 1
OTP bots are designed to socially engineer a victim into divulging sensitive information associated with online accounts.
Takeaway 2
OTP bots introduce automation to what used to be a manually intensive social engineering process.
Takeaway 3
To combat the threat of OTP bots, leverage threat intelligence to detect and remediate compromised accounts.
New Account Takeover Tactics
What is an OTP bot?
Understanding the Threat
How does an OTP bot work?
To illustrate how OTP bots operate, consider an example of a fraudster attempting to take over a victim’s online bank account and withdraw funds. The first step to defraud the victim is to obtain his or her online banking credentials and mobile phone number. Such information is available for a criminal operating a botnet or can easily be purchased on various Dark Web forums and markets. Then, the fraudster subscribes to an OTP bot service. Fees for these services range widely, from $100 for a one-week unlimited-use subscription to $4,000 for a lifetime unlimited-use subscription.
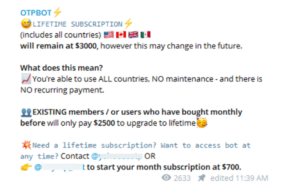
“Underground” Telegram Channel offering OTP bot subscriptions for worldwide banking fraud
After purchasing a subscription, the fraudster receives a token to activate the OTP bot and can begin working. The fraudster attempts to log in to the victim’s online bank account and, at the same time, prompts the bot by inputting the victim’s phone number and the name of the financial institution the victim is banking with. Finally, the bot will initiate a call to the victim and attempt to manipulate the victim to provide the 2FA code and other information as needed. The following is an illustrative transcript of a call made by an OTP bot to engineer a victim into unwittingly compromising their own account socially:

With more sophisticated bots, the fraudster can customize the messages delivered to the victim. For example, one very advanced OTP bot service offers an “Alternative Mode,” which allows the fraudster to solicit additional details during the call such as SSN, date of birth, and CVV even request any other information of interest. In this mode, the fraudster also can add or remove the 2FA capture. Another model, “PGP mode,” allows the fraudster to speak directly to the victim and even includes holding music before a call is connected. The “Pay Mode” lets the fraudster link a credit card (presumably a stolen one) to a Samsung or Apple Pay wallet.
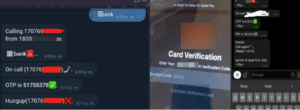
OTP bot call results as seen from a fraudster’s point of view
A Growing Threat
How do OTP bots scale?
OTP bots introduce automation to what used to be a manually-intensive social engineering process. Instead of contacting victims individually by phone or SMS, OTP bots do the work automatically and at scale. This implies more account takeover (ATO) attacks and more victims. As a result, the returns for fraudsters using OTP bots are high and correlate with the volume of prospective victims targeted. The more victims targeted, the greater the gains. Many threat actors have reported great success with OTP bots. For example, a subscriber of a leading OTP bot service claimed that he made $50,000 in one month.
Consequently, OTP bots are driving substantial losses for financial and other institutions. Several factors are driving this. First, the bot calls are skillfully crafted, creating a sense of urgency and trust over the phone. The calls rely on fear, convincing victims to act to “avoid” fraud in their accounts. Second, victims are accustomed to providing a code for authentication as it has become common practice for companies to request a verification code when speaking with a call center representative.
What Financial Institutions Can Do
Recommendations to combat OTP bots
To combat the threat of OTP bots, it is important to recognize that threat actors use OTP bots after they already have access to a customer’s account. That customer’s account may have been compromised due to a malware infection, credential stuffing attack, or another means of account compromise. As such, we recommend organizations go “up the chain” and identify accounts at risk of compromise. Specifically, organizations can leverage intelligence sourced from the Dark Web and other ‘underground’ sources to proactively identify customer accounts at high risk of account takeover and action them to mitigate that risk. This will preempt a takeover attempt and the associated OTP bot attack.
Additionally, we recommend educating customers at different touchpoints (e.g., email, call center interaction) about social engineering scams. Customers should be wary when receiving unsolicited calls or text messages and being asked to confirm a 2FA code. Customers should be encouraged to call the corporate call center (e.g., by calling the phone number on the back of a debit/credit card) to confirm that they are, in fact, speaking with an authorized representative.





